Connecting devices from far away, especially those little Raspberry Pi units doing important work, really brings up some thoughts about safety. You want to make sure your remote IoT setup, like a sensor watching your plants or a tiny camera, stays private and works just for you. Getting your Raspberry Pi to securely connect remoteIoT P2P SSH Raspberry Pi means keeping it free from danger, in a way that avoids anyone or anything being harmed by any risk, danger, or threat. It's about making sure your data is safe and protected against harm or unauthorized eyes.
So, when we talk about making things "secure," we mean setting them up so they are free from danger or attack. This is particularly important when you have devices out there, perhaps in a garden shed or a distant workshop, that need to talk to each other or to you. You want to know that your connection is firm, like her papers were secure in the vault, and that no one can listen in or mess with what your devices are doing. It's a big deal for peace of mind, really.
This article is going to walk you through how to set up a peer-to-peer (P2P) SSH connection for your Raspberry Pi devices, focusing very much on keeping things safe. We will look at the steps to get this working, and also talk about some smart ways to make sure your remote IoT connections are truly protected. You know, free from the risk of being intercepted or listened to by unauthorized persons, which is pretty much the goal here.
Table of Contents
- Why Keeping Things Safe Matters for Your Remote IoT
- What Peer-to-Peer SSH Is and How It Helps
- Getting Your Raspberry Pi Ready for Secure P2P SSH
- Important Security Steps to Always Take
- Common Questions About Secure Remote Pi Connections
- Making Your Remote IoT Connections Truly Safe
Why Keeping Things Safe Matters for Your Remote IoT
When you have a Raspberry Pi out there, maybe gathering data or controlling something, it's pretty much like having a tiny computer with a job. So, you want to make sure it's free from danger, damage, or anything bad happening to it. The meaning of secure is free from danger, and that's exactly what we aim for with these connections. If someone unwanted gets access, they could mess with your data, take over your device, or even use it for their own purposes, which is obviously not good.
In a way that is safe or protected against harm, crime, etc., your connection needs to be solid. Think about it: if your remote IoT device is controlling a water pump, you wouldn't want someone else turning it on or off without your say-so. Or, if it's collecting sensitive information, you need to know that information is free from the risk of being intercepted or listened to by unauthorized persons. This level of protection helps keep your projects running smoothly and your information private, too it's almost a necessity these days.
Securely, as we know, can be defined as a state or manner of being safe, free from danger, harm, or risk. That's why every step you take to connect your remote IoT Raspberry Pi devices needs to keep this idea in mind. It's not just about getting them to talk, but about making sure they talk in a manner free from danger, so that you maintain control and peace of mind. Check all personal items are securely handled, and that goes for your digital items too, you know?
What Peer-to-Peer SSH Is and How It Helps
So, let's talk about how these connections actually work. When we say "peer-to-peer" with SSH, we're talking about a direct connection between your computer and your Raspberry Pi, or even between two Raspberry Pis. This is different from going through a central server or a cloud service, which can sometimes add extra steps or potential points of weakness. It's about creating a more personal, direct link, that is that.
SSH: A Familiar Friend
SSH, or Secure Shell, is a method for secure remote access to computers. It's like having a very secure telephone line to your Raspberry Pi. When you use SSH, all the information exchanged between your computer and the Pi is encrypted, meaning it's scrambled so that only the intended recipient can read it. This helps keep your commands and data private. It's a widely trusted tool for managing Linux-based systems, which the Raspberry Pi uses, and has been around for quite a while, so it's very reliable.
The core idea of SSH is to provide a way to interact with a remote device as if you were sitting right in front of it, but with the added benefit of a secure channel. This means your login details, the commands you type, and any files you transfer are all protected. It's a foundational piece for any remote access, and it helps your connection be free from risk of loss, which is pretty important for remote work.
The Peer-to-Peer Difference
Now, P2P SSH takes this secure connection concept and applies it directly. Instead of needing to set up complex port forwarding on your home router, or relying on a third-party service that might introduce its own issues, P2P aims to let devices talk directly. This can simplify things a bit for remote IoT setups, especially when you have multiple devices that need to communicate without a central hub. It's about creating a more straightforward, direct path for communication, more or less.
This directness can mean less latency and potentially fewer points where something could go wrong, or where an unwanted person might try to get in. It's about giving your devices the ability to establish a safe link without a middleman, which can be very appealing for small, independent IoT projects. For instance, if you have two Raspberry Pis in different locations that need to share data, P2P SSH could be a very clean way to do it, you know?
Getting Your Raspberry Pi Ready for Secure P2P SSH
Setting up your Raspberry Pi for secure P2P SSH involves a few key steps. It's not overly complicated, but each part plays a role in making sure your connection is free from danger, as we discussed earlier. We want to make sure you're doing this in a way that avoids someone or something being harmed by any risk, danger, or threat, so let's get into the practical side of things.
Initial Pi Setup for Security
Before you even think about P2P, you need to make sure your Raspberry Pi itself is set up with good security habits. First, always change the default password. This is perhaps the most basic but most important step. A default password is like leaving your front door unlocked; anyone who knows it can just walk in. So, pick something strong and unique, something hard for others to guess, that is that.
Next, make sure your Raspberry Pi's operating system is up to date. This means running commands like `sudo apt update` and `sudo apt upgrade`. Keeping your software current helps patch up any known weaknesses that could be exploited. It's like checking all personal items are securely put away; you're tidying up potential vulnerabilities. This is a simple step, but one that often gets overlooked, actually.
Also, it's a good idea to disable any services you don't need running on your Pi. Every running service is a potential entry point, so if you're not using it, turn it off. This reduces the "attack surface" for anyone trying to get in. Think of it as closing windows you don't use; fewer open windows mean fewer ways for someone to sneak in, in a way.
Setting Up SSH Keys for a Tighter Grip
Using SSH keys instead of passwords for login is a much more secure method. It's like having a special, very complex key that only you and your Raspberry Pi possess, rather than a password that could potentially be guessed or stolen. SSH keys come in pairs: a public key that you put on your Raspberry Pi, and a private key that stays on your computer and is never shared. When you try to connect, the two keys talk to each other to confirm it's really you.
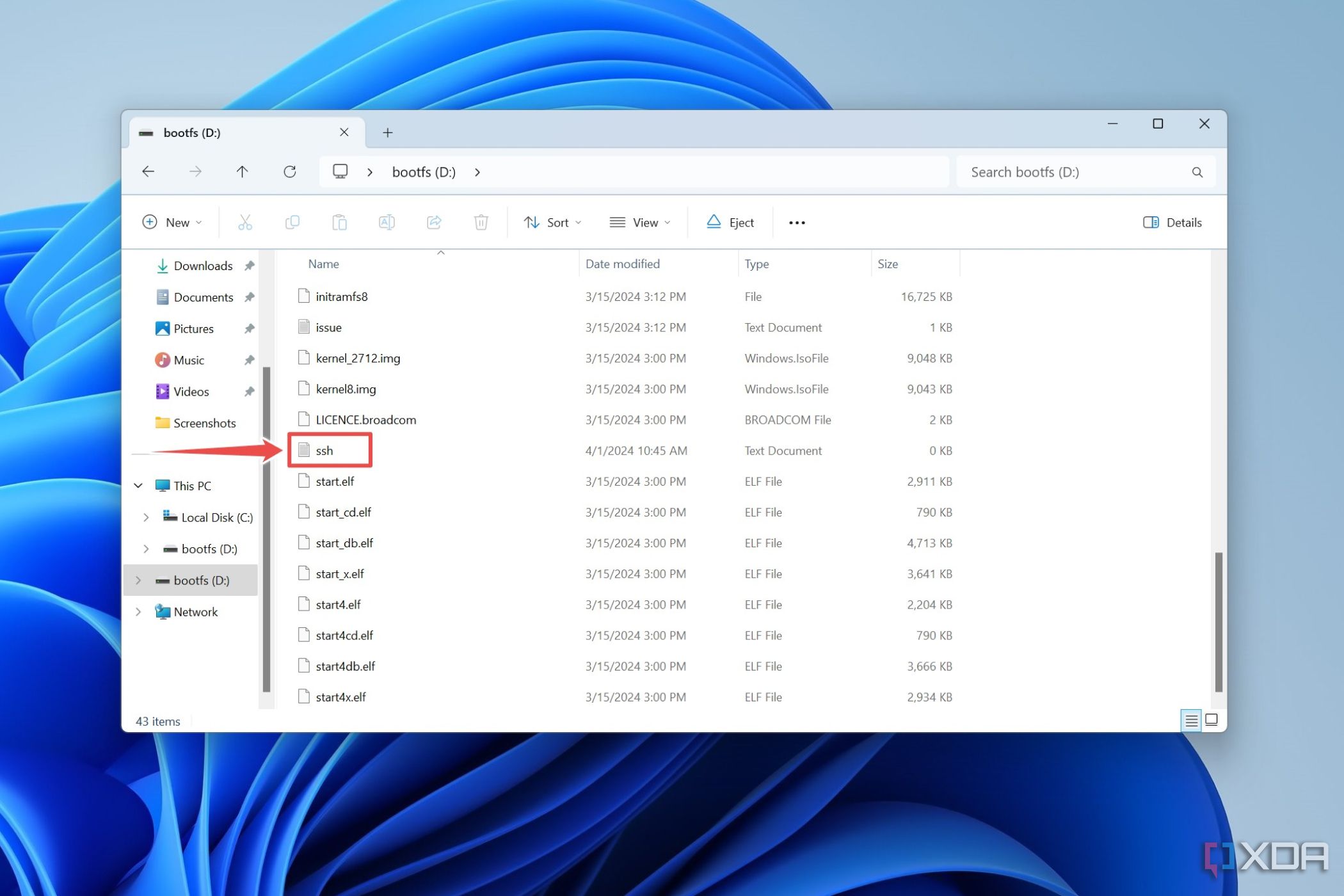
To set this up, you'll generate the key pair on your local computer. Then, you copy the public key over to your Raspberry Pi's `~/.ssh/authorized_keys` file. Once that's done, you can configure your Pi to only allow logins using SSH keys, completely turning off password-based logins. This is a very strong step towards making your connection free from the risk of being intercepted or listened to by unauthorized persons. It's a bit more work initially, but it provides a significantly higher level of protection, you know?
You can find many guides online for generating SSH keys, but a typical command on your computer might be `ssh-keygen`. Then, to copy the public key to your Pi, you could use `ssh-copy-id user@your_pi_ip`. After that, remember to edit the SSH configuration file on your Pi (`/etc/ssh/sshd_config`) to disable password authentication by setting `PasswordAuthentication no`. Then, restart the SSH service with `sudo systemctl restart ssh`. This makes things much safer, genuinely.
Making P2P Connections Possible
For true P2P SSH without port forwarding or a VPN, you'll often need a tool that helps devices find each other across different networks. Services like ZeroTier or Tailscale create a virtual network layer, making it seem like all your devices are on the same local network, even if they are miles apart. This is a really clever way to achieve P2P connectivity without opening up your home network to the wider internet, which is a common security concern.
With a tool like ZeroTier, for instance, you install the client software on both your computer and your Raspberry Pi. Then, you join them both to a unique network ID that you create on the ZeroTier website. Once they are on the same virtual network, they can talk to each other directly using their virtual IP addresses, just as if they were side-by-side. This means your SSH connection is still encrypted by SSH itself, but the P2P aspect is handled by the virtual network, making it much simpler to establish a connection that is safe or protected against harm. It's a pretty neat solution, honestly.
Setting up these virtual networks usually involves a few commands to install the client, then one to join your network, and perhaps another to authorize the device on the service's web interface. Once connected, you can SSH to your Pi using its virtual IP address, like `ssh pi@10.147.17.123`. This method helps you securely connect remoteIoT P2P SSH Raspberry Pi without needing to tinker with your router settings, which can be a relief for many people, basically.
Important Security Steps to Always Take
Even with SSH keys and P2P tools, there are always extra steps you can take to make your setup even more secure. Remember, securely can be defined as a state or manner of being safe, free from danger, harm, or risk. These additional practices help reinforce that state, making it even harder for anything unwanted to happen. It's about layered protection, you know?
Keeping Software Up-to-Date
We touched on this before, but it's worth saying again: regularly update your Raspberry Pi's operating system and all its software. Software updates often include security patches that fix newly discovered weaknesses. Running outdated software is like leaving a known weak spot in your defenses. Make it a habit to run `sudo apt update && sudo apt upgrade` regularly, perhaps once a month or whenever you access your Pi. It's a very simple thing to do, yet it makes a big difference in keeping things safe, you know?
Strong Passwords and Key Phrases
While SSH keys are great, you'll still need a strong password for your Pi's user account and, crucially, a strong passphrase for your private SSH key. If someone gets hold of your private key, a strong passphrase will still protect it. A good passphrase is long, includes a mix of different character types, and isn't easily guessable. Think of it as an extra lock on an already secure vault. It's just another layer of safety, as a matter of fact.
Limiting Access Points
Only allow SSH access from specific IP addresses if you can. If your home IP address is static, you can configure your Raspberry Pi's firewall (using `ufw` for example) to only accept SSH connections from that particular address. This means even if someone somehow figures out your Pi's virtual IP and has a private key, they still couldn't connect unless they were coming from your allowed location. This is a very powerful way to restrict who can even attempt to connect, and stuff.
For instance, you might use commands like `sudo ufw allow from your_home_ip to any port 22` to set this up. This step really narrows down the potential for unwanted connections. It's about being free from danger or attack by cutting off many possible routes. It's a smart move for any remote device, obviously.
Monitoring Your Connections
Keep an eye on who is connecting to your Raspberry Pi. You can check SSH logs for unusual login attempts or activity. Tools like `fail2ban` can automatically block IP addresses that try to guess your password too many times (though this is less relevant if you've disabled password login, it's still good for other services). Being aware of what's happening on your device helps you spot any potential issues early. It's like checking all personal items are securely in place; you're verifying that everything is as it should be, more or less.
Regularly reviewing logs, perhaps with `journalctl -u ssh` or by looking at `/var/log/auth.log`, can give you insights into who has tried to connect and when. If you see anything suspicious, you can take action quickly. This proactive approach helps keep your system free from danger or risk of loss, and it gives you a sense of control over your remote devices, which is pretty nice.
Common Questions About Secure Remote Pi Connections
People often have questions when they're thinking about connecting their Raspberry Pi devices from afar, especially when security is a big concern. Here are a few common ones, and some thoughts on them.
How do I securely access my Raspberry Pi from outside my network?
The best way to securely access your Raspberry Pi from outside your local network involves using SSH with key-based authentication, rather than passwords. Then, to bridge the network gap, you can use a virtual private network (VPN) or a virtual networking service like ZeroTier or Tailscale. These services create a secure tunnel or a virtual network that makes your remote Pi appear as if it's on your local network, letting you connect securely without opening up ports on your router. It's a very common and effective method, actually.
Is SSH safe for remote IoT devices?
Yes, SSH is generally considered safe for remote IoT devices, provided it's configured properly. The "secure" in Secure Shell means it encrypts all communication, protecting your data and commands from being intercepted. However, its safety depends on your practices: always use strong, unique SSH keys, disable password authentication, keep your Pi's software updated, and consider using a firewall. If you follow these steps, it helps ensure your connection is free from danger or harm, so it is quite safe.
What is peer-to-peer SSH?
Peer-to-peer (P2P) SSH refers to establishing a direct SSH connection between two devices, like your computer and your Raspberry Pi, without needing a central server or complex port forwarding on your router. This is often achieved by using virtual networking services (like ZeroTier or Tailscale) that create a virtual local network over the internet. These services allow your devices to find and communicate with each other directly, even if they are in different physical locations, making it a very direct and often simpler way to securely connect remoteIoT P2P SSH Raspberry Pi.
Making Your Remote IoT Connections Truly Safe
Getting your remote IoT Raspberry Pi devices to communicate securely is about being thoughtful with your setup. It's about applying the idea of "securely" – in a manner free from danger – to every part of your connection. From using strong SSH keys to keeping your software current, each step adds a layer of protection, making sure your projects stay private and under your control. This approach helps ensure your connections are free from risk of loss, and that your digital interactions are safe, just like you'd want your physical belongings to be. You can learn more about Raspberry Pi projects on our site, and if you want to explore more about general network security, check out this page for other tips.
As of today, October 26, 2023, these methods remain very effective ways to keep your remote Raspberry Pi connections private and protected. The world of connected devices is always changing, but the core principles of keeping things safe stay the same. By following these suggestions, you're doing a great job of making sure your Raspberry Pi devices are connecting in a way that is safe or protected against harm, crime, etc. It's a continuous process, but one that's definitely worth the effort for your peace of mind, very much so. For more information on secure practices, you might find it helpful to look at resources from organizations focused on internet security, for example, the National Cyber Security Centre offers good general advice.


Detail Author:
- Name : Prof. Milan Block III
- Username : rosalee98
- Email : blake.erdman@gibson.biz
- Birthdate : 1996-05-01
- Address : 266 Josie Tunnel Suite 820 Eulaliamouth, AL 82371-3343
- Phone : +1-573-233-2703
- Company : Schaden Group
- Job : Signal Repairer OR Track Switch Repairer
- Bio : Earum aspernatur magni et et omnis laboriosam. Officiis laboriosam cum quia quas. Sint iusto rem voluptates dolorum doloremque hic. Tempora sunt in iste aut nihil doloremque quo fugiat.
Socials
instagram:
- url : https://instagram.com/isac_id
- username : isac_id
- bio : Qui voluptatem doloremque accusamus velit sint ab. Ut ipsa adipisci odio quisquam fugit.
- followers : 336
- following : 1125
twitter:
- url : https://twitter.com/weberi
- username : weberi
- bio : Eos rerum rem cupiditate laborum nihil qui non facere. Doloribus doloribus officiis ut qui tenetur molestiae. Magnam qui molestiae quo.
- followers : 5514
- following : 410

